Ransomware does not discriminate.
Over 13.1 million U.S. citizens — 4% of the U.S. population — have been targeted by ransomware. Half are willing to pay a ransom of up to 00 to get their information back. These are your teachers, your employees, your doctors and your public administrators. No one is safe.

- A (Brief) History of Ransomware
- The Path of Destruction
- Ransomware Only Lurks in Dark Corners, Right?
- The Tech Behind the Terror
- Wait, What is BitCoin?
- I’ve Been Infected
- First Line of Defense
- Infographic
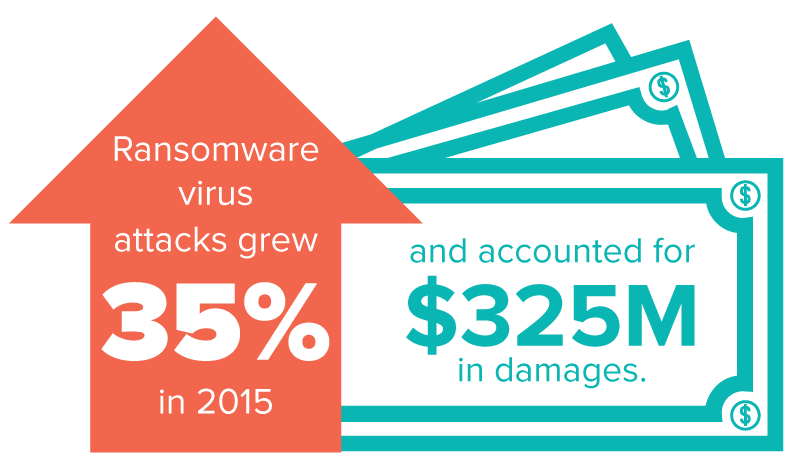
Hackers have been so successful that ransomware virus attacks grew 35% in 2015. The majority of these attacks are increasingly committed by encryption inducing ransomware. Cryptowall, a single strain of ransomware, has accounted for 25 million in damages alone since its discovery in January 2015.
In the United States, the ransomware virus infection rate in May 2016 was the second worst, only bested by April 2016, which had an infection rate increase of 159%, compared to the previous month.
With no easy solution to prevent or defeat an attack, cybercriminals are expanding ransomware to mobile devices and video games, hoping to spread their reach as far as possible.
Despite the increase in attacks, 32% of computer users unaffected by ransomware believe it won’t happen to them. And 50% claimed that if infected, they would be willing to pay the ransom.
With one-third of the population believing they won’t be infected, it’s no wonder that cybercriminals are leveraging ransomware as a steady revenue source.
So, how can you prepare? When it comes to ransomware, the old cliche stands: knowledge is power. A Bitdefender study revealed that half of participants could not identify ransomware, yet two-thirds knew that ransomware posed a threat to their computers.
Knowing the history, strains and signs of a ransomware attack is the first step to effective ransomware prevention.
It’s time to arm ourselves.
“Online criminals have found a sweet spot with ransomware. As long as they can find people who are willing to pay, they will continue to push these infections worldwide.”— Enigma Software Group spokesperson Ryan Gerding
From 1989 to 2016: A (Brief) History of the Ransomware Virus
In 1989, the first ransomware surfaced. The Cyborg Trojan, written by Dr. Joseph Popp, was dispatched to subscribers of PC Business World. A floppy disk promising some new software arrived in a seemingly harmless mass mailer.
Once the software was installed from the disks, the subscribers were alerted that their device was infected, and in “X” number of reboots (usually 90) the software would demand payment. If the subscriber didn’t pay up, they would be locked out from their computer.
This primitive ransomware virus contained one major flaw. It used a symmetric encryption method. Symmetric encryption essentially uses the same key to decrypt the data as it did to encrypt it. Thus, the decryption key could be found somewhere within traces of the virus or infected computer.
It wasn’t until 1996, when Adam Young and Moti Yung launched a concept attack against the Macintosh, that the idea of a cryptoviral attack was born.
Bonnie and Crypto
Today, there are a myriad of ransomware strains. Each one aims at stealing hard earned money from innocent users. Or worse: hackers steal your credit card or personal identity information.
Major revenue-generating scams include misleading apps, fake antivirus scans, locker ransomware and crypto ransomware. The later two are the primary forms of ransomware in circulation today.
Locker ransomware denies the user access to their device and locks it. Normally, the language asks the victim to pay a “fee” and uses voucher payment, such as pre-paid electronic gift cards. Locker ransomware originated as a social engineering tactic. An example of this is a lockerware strain known as the FBI Moneypak virus.

The FBI Moneypak virus first manifests when a warning pops up on the screen saying the computer has been locked. It then claims that the FBI has locked down the computer because the IP address was traced to viewing or distributing pornographic content, or has distributed copyrighted items (music, videos, or software) against the law.
The virus is intended to scare the user into believing there is a grave mistake with the federal government and they can avoid a confrontation if they pay a fee to counter their illegal actions. Otherwise, violators would face jail time.
On the other hand, crypto ransomware does not lock the computer but instead encrypts any files associated with the user, networks and shared drives. For many, this is considered even more dangerous.
As the virus spreads through the network, each infected computer represents thousands or millions in downtime and lost revenue. Businesses are crippled as the virus jumps from computer to computer.
Crypto strains are also harder to detect because paying the ransom involves using the dark web browser, Tor, as well as paying anonymously through bitcoins. Infamous strains of cryptoware include CryptoLocker, TeslaCrypt, CryptoWall and Ransomware32 (the first ransomware written in JavaScript).
The Path of Destruction
Ransomware targets and exploits organizations in the education, healthcare or government-related industries. Some of the most publicized ransomware attacks are concentrated in these industries — and this is no coincidence.
Hackers have targeted small town police networks across America, compromising traffic and mugshot databases. In April of 2014, the City of Detroit was attacked by cryptoware. An entire database was held for a ransom of 00,000. Detroit’s saving grace: the database was outdated. The city did not pay the ransom, and took the attack as a warning.
Others have not been so lucky.
Hollywood Hospital paid 7,000 (about 40 bitcoin) after hackers seized control of a network sector. The virus rendered certain infected computers on their hospital network unreachable. Doctors, nurses and patients suddenly had no access to records. The hospital administration decided the best course of action was to pay the ransom:
“The malware locks systems by encrypting files and demanding ransom to obtain the decryption key. The quickest and most efficient way to restore our systems and administrative functions was to pay the ransom and obtain the decryption key,” [Chief Executive of Hollywood Hospital] Stefanek said. “In the best interest of restoring normal operations, we did this.”
While it was in the best interest of the hospital to resume normal operations, paying the ransom cures only the symptoms. The hospital does not find where the breach originated. Furthermore, paying the ransom trusts that the criminals adhere to moral guidelines and respond honestly.
Paying the ransom also encourages further ransomware attacks. But since ransomware is specific to each hacker, other organizations may not have such luck getting their info back.
Following the Hollywood Hospital attack, the second largest recorded ransom payment in 2016 belonged to the infected systems of South Carolina school district, Horry County. After 25 servers were decrypted, the FBI was called to the district for an investigation of the source.
However, the FBI could find no alternative course of action other than paying the ransom. Once again putting faith in the hackers, the school district paid ,500 to decrypt the servers.
While these headlines may seem distant to a business owner or American citizen, these are the faces of the thousands of organizations and individuals attacked by ransomware annually.
“The whole experience was frustrating, annoying and expensive both in a loss of time and in the cost of the antivirus programs to prevent it from happening again,” said Kara Buntin, owner of A Cake To Remember, when discussing her personal experience with a ransomware attack. She commented on how she was glad that the ransomware reached her home instead of her business. Kara recognized had the ransomware struck her business, it would’ve been disastrous.

Ransomware only lurks in dark corners, right?
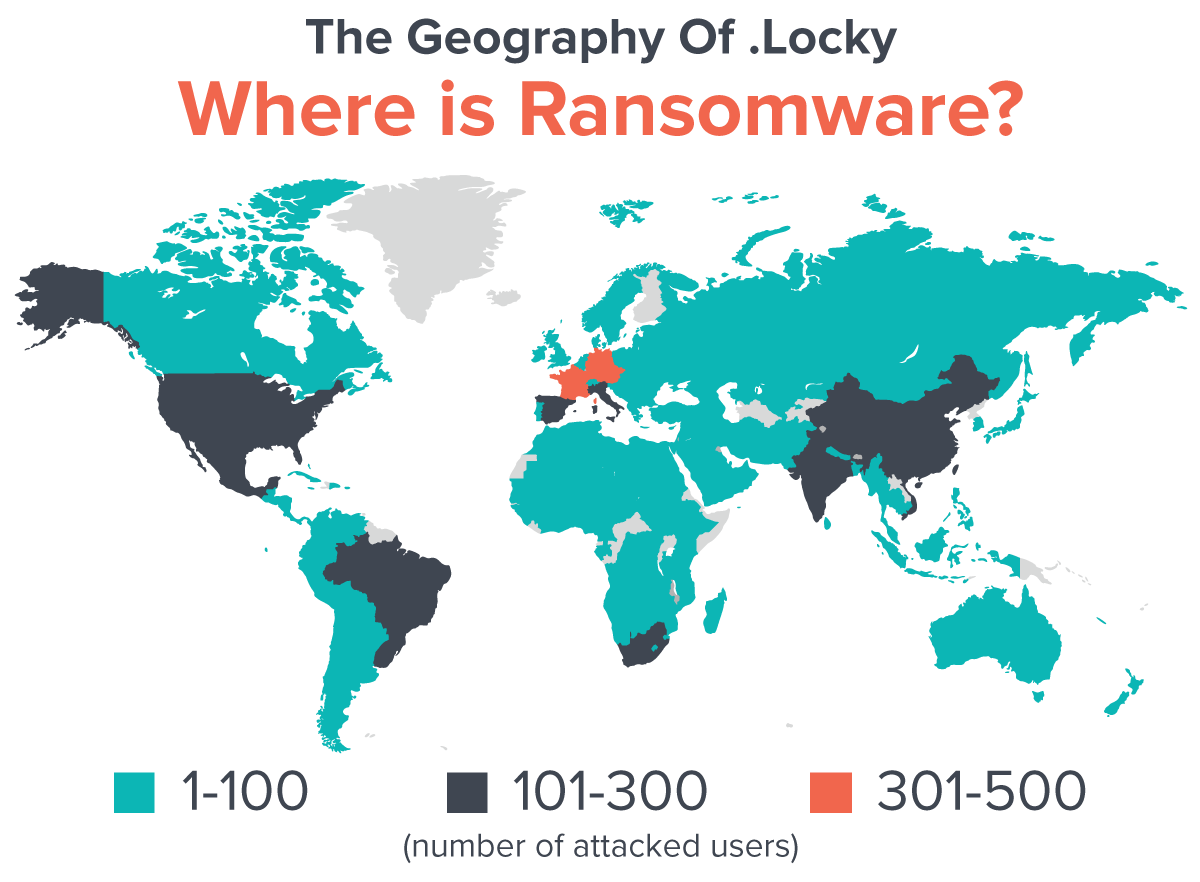
Ransomware is a global epidemic with attacks in over 100 countries. The .locky strain alone has attacked in France, Germany, USA and India, for a combined total of 1,300 users including businesses and government organizations. This is three months after its first public attack on the Hollywood Hospital. With so many strains, where should users look for ransomware?
Target #1: Malvertising
Hidden in plain sight, ransomware is buried in the code of malvertising. Malvertising finds flaws in advertising software, such as Adobe Flash or Microsoft Silverlight, and loads ransomware code while the actual advertisement is loading. Ironically, when ranked by vertical, 23.2% of the exploited businesses are actually technology websites.
For consumers, malvertising is stereotypically found on old, or poorly designed websites. Thus, any user may avoid seemingly “sketchy” looking sites. Yet shockingly, highly-trafficked sites such as NFL, The New York Times and BBC have reported malvertising with ransomware code traces.
Consumers have begun to install AdBlock to not only prevent malvertising, but eliminate intrusive marketing altogether. The result is a decline in sponsored advertising revenues for any website. Forbes website was suffering from this decline.
In response to this dilemma, Forbes asked visitors to turn off all ad blockers before entering their site. This action, while helpful to Forbes, puts consumers in danger of a ransomware attack. Despite this, 50% of website guests did disable their ad blocker.
A few months after this data was collected, Forbes discovered that malvertising was present on their website. For the 50% of visitors who decided to turn off their ad block, their computers were indeed at risk of infection.

A simple search of the advertised company can yield the same results, and bypass any malvertising code embedded in the ad.
Consider installing a trusted ad blocker or antivirus software to block malicious ads. Do not turn it off, even for legitimate sites.
Target #2: Mobile
Recently, ransomware hackers have branched out to infecting mobile devices, affecting both Apple and Android users. These threats, arising from bootlegged developer software and phishing apps, as well as vulnerabilities on Apple’s AirDrop function, have lead to escalating ransomware threats.
Security company Symantec predicts that hackers will continue to create and adapt ransomware to fit iPad and iPhone products. This is attributed to the higher income level of Apple’s demographic — higher income level increases the likelihood of a large payout.

Target #3: Emails
The email landscape is more perilous than ever, as 93% of phishing emails contain some form of ransomware. Phishing emails are becoming trickier to decipher from legitimate sources.
Hackers are sending emails that use multiple languages and appear to be from existing companies in the target’s country.
Many emails include Microsoft Word (.doc) attachments that require macros to be enabled. Permitting macros allows ransomware to infect the computer.
Some emails don’t include attachments but rather links to fill out a form, call a phone number or even unsubscribe. Regardless of the format, Americans are the most sought-after email targets.
According to a Bitdefender study, 61.8% of all malware U.S.-bound emails contain some form of ransomware. France and the UK are the second largest targets.


Target #4: Video Games
Teslacrypt, a new member of the ransomware “family,” produced strains that target saved-game content and even creates “extra” downloadable content files. Targeted games include Minecraft, Call of Duty, EA Sports and Dragon Age.
Teslacrypt includes new functionality to accommodate users by processing ransom payments through PayPal My Cash cards. However, using this feature increases the ransom from the average 00 to ,000.
There is good news for those affected by TeslaCrypt. In May 2016, TeslaCrypt developers released the master decryption key and moved to distributing CryptXXX ransomware. Despite the appearance of another strain, those who would stumble on an old strain of TeslaCrypt now have hope.
Decoding platforms are reportedly being updated so that users with files ending in .xxx, .ttt, .micro and .mp3 can now have these files decrypted.
The Tech Behind the Terror
Ransomware appears to be everywhere, but how does a virus with so many strains work? In order to examine the general operations of ransomware, we will look at the .locky strain.
Imagine sorting through your inbox when you come across this email.
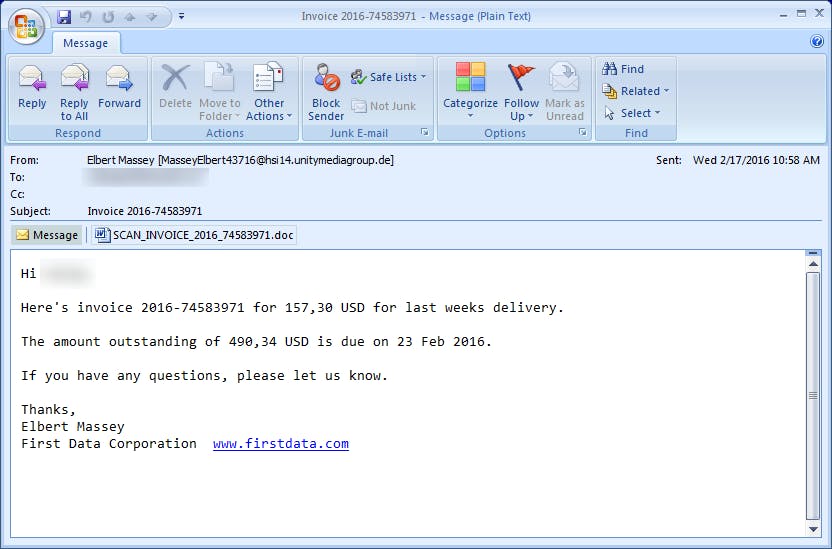
A Nigerian prince isn’t asking for bank account information, so all seems well at first. With so many invoices coming across your inbox you decide it is worth the risk to open the document, rather than be charged a late fee for an unpaid invoice.
Next, you may see a Word document that will kindly ask you to enable macros so the invoice can be read. Or, you may have the option to manually open files in a .zip file. Shortly after completing these tasks, the following message may appear on your screen.
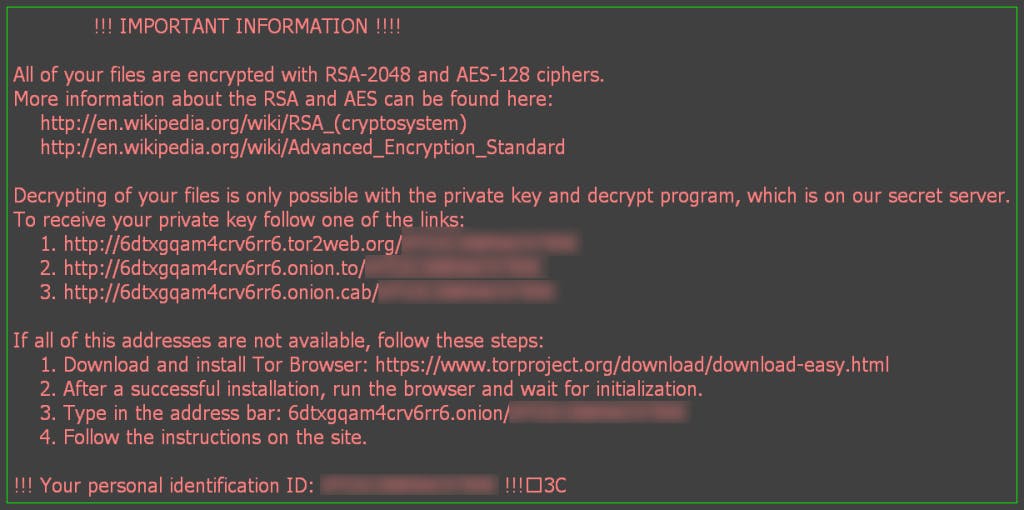
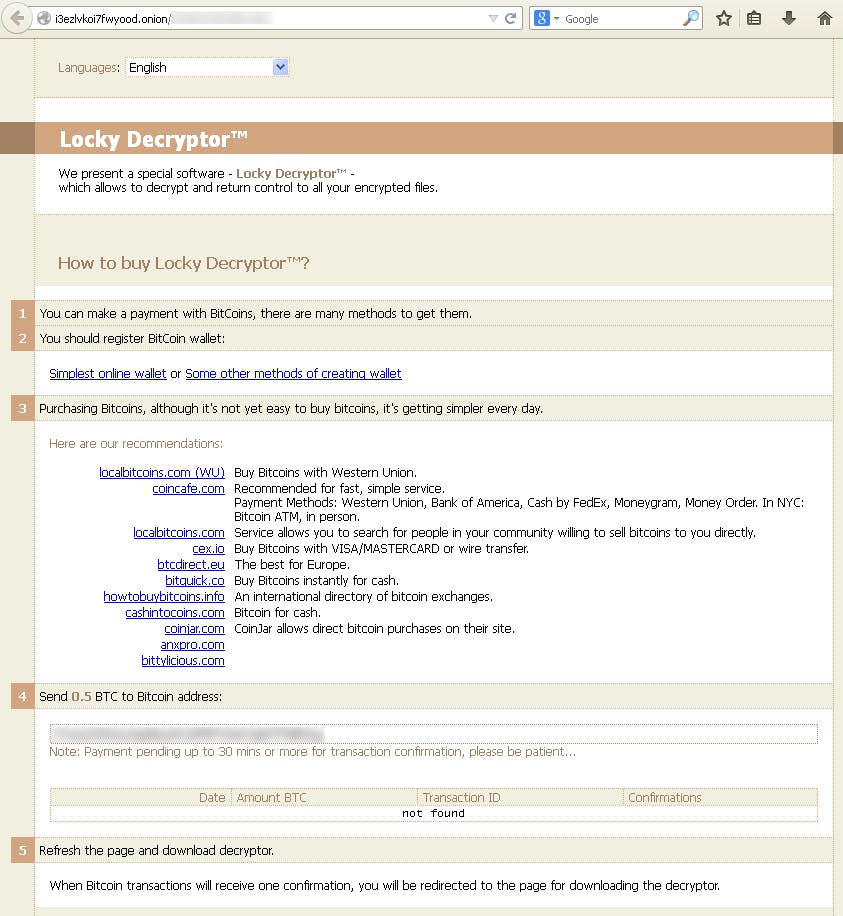
You have been infected by crypto-ransomware. The hackers are now demanding bitcoins in exchange for your files.
“The common theme is panic. On the business side, they have lost countless hours of work, deadlines need to be met and money will potentially be lost. On the consumer side, the person is mostly concerned about losing all of the videos and pictures that she had taken of her family over the years. Especially her grandchildren. The reality is that ransomware victims are on the ledge, have no idea what to do and are concerned that all their data will be lost.”— Lawrence Abrams, owner of BleepingComputer.com
Wait, What is Bitcoin?
In the advent of the digital age, hackers are now relying on bitcoins. Before July 2010, there was no market for bitcoins. Thus, this digital currency is a new player in the cyber community. Bitcoin was proposed by the elusive software developer Satoshi Nakamoto.
Banks do not print bitcoins. Instead, bitcoins are “mined” through a process of using computers to solve mathematical problems. What gives bitcoins their value? Only 21 million can ever be mined. As of February 2016, 15 million were already mined. It is predicted that the remaining 7% will be mined over a period of 100 years.

What makes bitcoins attractive to hackers? The currency is decentralized, so law enforcement could not track it to a sole source. It is anonymous, so hackers can’t be traced.
Hackers also safeguard their anonymity by using the dark web browser Tor. Transfer is fast, and requires only minuscule fees for international transfer. Compared to the risks that banks may carry, bitcoins are the choice currency for hackers.
The price of bitcoins has increased steadily the past months. When Hollywood hospital paid a 40-bitcoin ransom in February 2016, the ransom was valued around 7,000 or around 25 per bitcoin. At of the beginning of June 2016, the price per one bitcoin was 83, making Hollywood hospital’s ransom valued around 3,320 today.
I’ve Been Infected: What Are My Options?
Option #1: Pay Up
“Just pay the ransom,” say the FBI. The FBI warns that attacks involving Cryptowall, Cryptolocker and other variations are difficult to track and decrypt. Instead, the FBI suggests paying the ransom.
While we see this decision executed by major hospitals and organizations, ultimately this is a last resort and poor decision. Paying the ransom places trust in criminals, and gives a “green light” to revenue-seeking hackers.
Konstantinos Varsis, Director of Computer Being in London, works with multiple ransomware victims. He has witnessed the repercussions of paying the ransom: “Many times, the consequence of the action is they then become victims of credit card fraud and their data remains encrypted, despite the payment.”
Kansas Heart Hospital is a prime example of a failed decryption. The hospital was attacked by ransomware in May 2016. The attackers asked for a small ransom in exchange for their files.
Upon paying the ransom, the files weren’t decrypted. Instead the hackers extorted more money from the hospital by demanding a second, larger payment. The hospital did not pay the ransom figuring it was no longer a wise strategy.
Option #2: Stop, Drop and Roll for Ransomware
![]()
- Disconnect
– Disconnect from your network
– Turn off all Wifi and Bluetooth
– Remove any external drives, USBs or devices - Determine the extent of the damage
- Determine the ransomware strain
- Determine the best response
Hackers Do 3 Things: Encrypt, Delete or Lock
Hackers threaten to do one of three things: encrypt, delete or lock. First, if a hacker wishes to encrypt your files, there are two different variations for doing this: symmetric or public/asymmetric.
The symmetric method uses the same key to encrypt and decrypt the files, while the public/asymmetric method uses a key to encrypt the data, and another to decrypt. The strengths of these passwords are measured in bits, and the longer the password, the harder it is to crack. A 20-bit key could take hours to crack, yet a 128-bit key would take months.
Today, sophisticated ransomware strains use a combination of symmetric and asymmetric keys for speed and security.
The most devastating threat is file deletion. FileCoder or GPcode strains threaten the loss of your files if the ransom is not paid. There is a small hope with these strains. Some attackers may take the easiest route of deletion and simply remove your files from appearing in your folders. However, some post-attack research has shown that traces may be left on the disk making partial recovery possible.
Finally, lockerware viruses typically present as a Law Enforcement warning. As discussed earlier, and example of this is the FBI Moneypak virus. The files are left in the same place, Trojan horses or scripts are used to lock network and internet access, and an unknown login is created.
Some basic strains of this virus can be removed from your hard drive using free versions of Malwarebytes and Hitman Pro.
First Line of Defense: What Hackers Don’t Want You to Know
With millions in damages, downtime and lost information, there has never been a greater need for cybersecurity. With 47% of ransomware outbreaks being spread to at least 20 people, what can you do to safeguard your network? Ransomware prevention can be boiled to three categories: educate, protect and monitor.
Education is one of the most necessary, yet highly underdeveloped areas of many major companies. Many forms of ransomware rely on phishing, which exploits human trust. After a Chinese hacking incident, the Wall Street Journal highlighted the crux of the security problem: “At least one employee will click on anything.”
Education
A simple way to incorporate education is by hosting “lunch-and-learns” with the Human Resources and IT departments. This quick meeting should train employees on the basics of spotting a phishing email and appoint a central authority to aid employees. It is essential that all computer users understand basic cybersecurity practices.

Tips for Educating Users
Protection
Thrive Technology Partners owner, Scott Kelly, has aided multiple businesses in ransomware prevention and recovery. However, he finds several firms fall victim to ransomware due to “classic lapses in common IT security practices: outdated desktop and server operating systems, antivirus software that was either expired, not business-class, or even installed; and no backups or disaster recovery solution in place. Having these solutions would help us evaluate if we would even need to pay the ransom.”
Preparing for a ransomware attack means backing up data often. The best backup follows the 3-2-1 rule: create 3 backup copies on 2 different media with 1 backup in a separate location. Furthermore, large businesses should consider using multiple storage solutions. Simply using on-premises storage or cloud will not prevent downtime in the event of an attack. Datto Inc. recommends adopting a hybrid cloud solution.

Tips for Protecting Users
Monitor
Ransomware virus attacks, data breaches, and rogue employees can all be spotted by consistent monitoring. Find a file or data storage solution that includes the ability to audit user activity.

Tips for Monitoring
“We tell our clients [who request admin accounts] to treat the access with great care and responsibility. We had a client [who abused this privilege] and all the company’s drives and folders were encrypted.” -Oli Thordarson, CEO of Alvaka Networks
The Future of the Ransomware Virus
Ian Trump, Security Lead at LOGICnow, believes the future of ransomware lies in iTunes and QuickTime for Windows. With a 40% market share and 106 known vulnerabilities, iTunes could prove to be a threat for consumers.
Currently, Adobe Flash leads the market in most vulnerable software. However, Google is actively removing the need for flash in content. Google has already started banning advertising requiring flash, in hopes to reduce malvertising.
The rise of ransomware attacks and collusion between hackers creates a formidable front. Yet, with the increase of ransomware strains, the topic of cybersecurity and ransomware prevention has been forced into the spotlight. Sharing resources and eliminating human errors can reduce the number of successful attacks.
Take action by educating, protecting and monitoring employees and data.
This is Part One in our two-part series on Ransomware. Here is part two, which is a detailed guide to how ransomware works and some technical safeguards you should take.

Check Out This Ransomware Infographic

