Many people want a penetration test for the wrong reasons. They don’t understand the true benefit of one. Here’s what a penetration test really does and how your business can use that information to improve your network security.
Penetration Testing Exposes Your Weaknesses
To the uninitiated, penetration testing can feel a bit like a public roast where you sit in a chair, drink wine, eat a fabulous dinner and give people turn after turn to mock and humiliate you. Why would you do that? Because it’s good for you – once in awhile.
By highlighting your technical vulnerabilities, your company will be able to respond and hence become much more secure. But, the mere sight of them is usually enough to make some business owners cringe.
What if you have an embarrassing hole in your security? A business partner can help you find and assess your risks. For instance, a Sec-Tec penetration testing report would expose your risk and tell you how to fix it. Within the larger penetration testing report, there are individual tests that help you identify vulnerabilities. Here are 3 types of tests in a penetration test that will expose your weaknesses:
Test 1: Infrastructure Testing
Almost all networks of any size are made up of only a few core components: clients, servers, switches and routers. Each of these devices may appear simple on the surface, but their associated operating systems and firmware contain tens of thousands of security-sensitive configuration options, which out of the box are typically configured for user friendliness and function over security.
A network infrastructure penetration test will look over the configuration of your core network components and identify weaknesses that could be exploited to compromise the confidentiality, integrity or availability of your systems and data. This could be a missing security update, a weak account or a default configuration option that is present for functionality reasons.
For example, many versions of Windows® Server OS have historically allowed anyone with network connectivity (no username or password needed) to obtain a complete list of usernames and groups present within the system. This may not sound like a big deal, after all a username is not much use without the matching password, but in a corporate network with tens of thousands of accounts, a list of usernames can massively increase the chances of finding an account with an identical username/password or blank password.
Yep, that “FridayTest/FridayTest” account created in a hurry when the accounts server went down months ago can be found again in seconds. And the penetration tester only needs to find one such account to start to gain access.
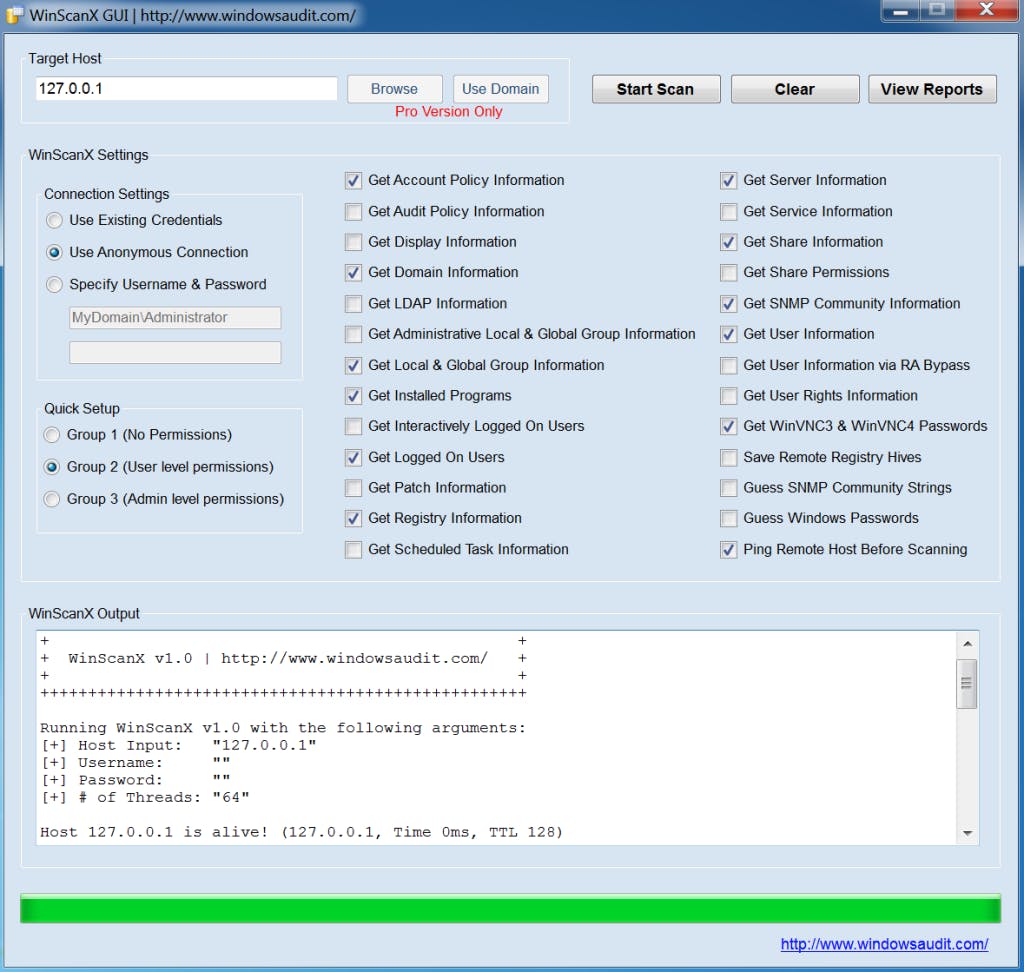
Freely available tools such as Winscanx can enumerate lists of users from Windows servers, and automatically attempt blank or identical passwords for each username identified.
Test 2: Application Testing
Most modern organizations have to expose their applications to the Internet: from online shopping carts to ordering portals and webmail. These applications present a sizable risk to the organization if they don’t follow security best practices. All too often security takes a backseat when these applications are developed, with user-friendliness and cost-savings the driving force behind the project. As a result, it’s often possible to perform unintended actions within the application.
Take for example the URL when viewing an online account:
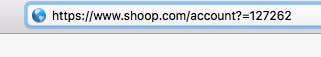
Now, this may appear innocuous to the uninitiated, but what happens if we change the account number in the URL to 127261, or 127260? If the application designers haven’t envisaged this, then you will be looking at the account details of an entirely different user.
Application security is such a big topic that entire standards, such as OWASP, have emerged for developers and testers to measure the security of applications against.
Test 3: Social engineering
Picture the scene, it’s Monday morning, the only things pounding louder than your headache are your deadlines. You receive the following email:
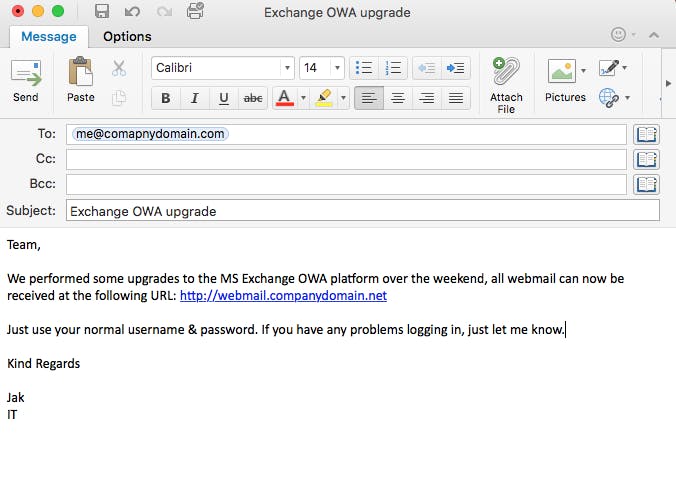
The domain looks about right, and Jak works in IT (in fact, we all know Jak works in IT thanks to his Linkedin Profile). You click on the link and you see the following:
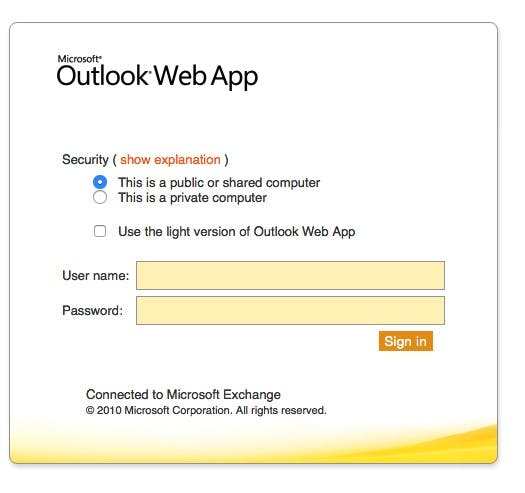
You test your account… Oh, what’s that? You wouldn’t? Well, you’re in a small majority. Simple social engineering assessments like this can often entice 40-50% of potential victims to click on the link in the email.
Most people simply don’t know how to validate an email or a link within an email and, relying on simple cognitive recognition, such as the familiar names in an email, will attempt the requested action without question.
Penetration Testing Shows You The Real Risk
Because a pen tester’s job is to reveal and take advantage of weaknesses, he or she is going to see what would happen if these weaknesses occurred in a real-world situation. At times, a weakness or vulnerability may seem high risk but because it may take a lot of work to pull off, it may be actually considered a medium or low risk. On the other hand, a low-risk exploit can be considered high-risk because it’s easy to do.
Penetration Testing Will Test Your Employee’s Resolve
One of the biggest risks is actually your employees.
Yes, your employees. Pen testers will employ software and hardware exploits, but they will also employ social engineering. Social engineering is a psychological tactic that bypasses technological weaknesses.
It relies on the fact that most people are good and decent and they want to help others – even strangers. To this end, a pen tester may try to exploit your network and other systems by pretending to be part of the staff, an IT service professional or a vendor.
You will know when the social engineering part of the test is being conducted, but your employees won’t.
Testers may try to infiltrate the office or some part of your business by asking for help or by acting helpless in front of your employees. For example, a tester may try to gain access to a secured area by asking an employee to help him or her move boxes into the facility. Or, the tester may ask for help with food or coffee or other beverages which the tester will say is for a co-worker or upper management.
When the tester gets the help he needs, he has successfully compromised your security through non-technical means.
Penetration Testing May Bring Down Your Network
This is something that surprises some business owners. When you get a penetration test done, there’s a good chance it will bring down your entire network for a day, or maybe even a few days.
That’s because the pen-tester needs to duplicate the attack of a real hacker. It may involve compromising systems, which means you don’t want those systems “live” and operational, lest a real hacker gets access to it during the test.
Conclusion
Securing your network and critical operations will lead to less downtime and disruptions to your customers and suppliers, leaving you with ample time to plan any next steps that need to be taken. Exposing weaknesses and vulnerabilities before failures occur will give you control over the outcomes and ample time to plan for contingencies. As scary as penetration testing is, and as daunting a task it may seem, any vulnerabilities that are exposed during the testing will prove these tools’ worth many times over.
LOCK DOWN YOUR NETWORK
FREE PENETRATION TESTING COURSE
- Social engineering
- Port scanning
- SQL injecting
- Anti-virus evading
- Client side attacking
About David Wray
David Wray is a certified TigerScheme SST, with 20 years of experience in technical Internet security. Beginning his career with the Peapod Group as a Firewall Engineer, David went on to found Sec-Tec Ltd in 2000, which specialises in penetration testing and technical assessment services. David is a guest expert on LBC radio, and can often be heard providing insight into information security news and current affairs.