Somewhere over the rainbow lies a land filled with mystery. Though not the Land of Oz, the Health Insurance Portability and Accountability Act (HIPAA) does seem filled with perilous flying monkeys that can hinder even the simplest means of file sharing.
So, how can healthcare firms, or even businesses overcome the difficult quest that is HIPAA compliant file sharing? This comprehensive guide will help you understand the HIPAA Technical Regulations that affect file sharing.
Does HIPAA Affect My Organization?
HIPAA regulations span many industries that use Personal Health Information (PHI). Even Prince’s death ushered in speculation on whether or not his HIPAA rights were violated when unauthorized healthcare sources contributed to celebrity gossip channels. So, it’s likely that if you have anything to do with PHI or with receiving PHI, you will have to follow HIPAA regulations.
All organizations that must comply with HIPAA regulations are known as “covered entities.” According to the Department of Health and Human Services “covered entities” include:
- Health Plans–including health insurance companies, HMOs, company health plans and certain government programs that pay for health care, such as Medicare and Medicaid.
- Most Health Care Providers—those that conduct certain business electronically, such as electronically billing your health insurance—including most doctors, clinics, hospitals, psychologists, chiropractors, nursing homes, pharmacies and dentists.
- Health Care Clearinghouses—entities that process nonstandard health information they receive from another entity into a standard (i.e., standard electronic format or data content), or vice versa.
But wait, HIPAA compliance doesn’t stop at covered entities. For many of those entities, third-party contractors will need access to your network or patient records. These entities are known as “business associates.”
- Companies that help your doctors get paid for providing health care, including billing companies and companies that process your health care claims
- Companies that help administer health plans: outside lawyers, accountants and IT specialists
- Companies that store or destroy medical records
While business associates are not held to the same standard, contracting with a regulated industry can prove a necessary hassle. If a covered entity or business associate intends to share files, then they must meet certain benchmarks that constitute HIPAA compliant file sharing.
So, regulations are everywhere — kind of like flying monkeys. How can your firm prepare? Let’s break down HIPAA’s technical safeguards into digestible, actionable items.
The Three Security Standards
Within the HIPAA regulations, there are a set of security standards. These standards are broken down into three categories: administrative, physical and technical.
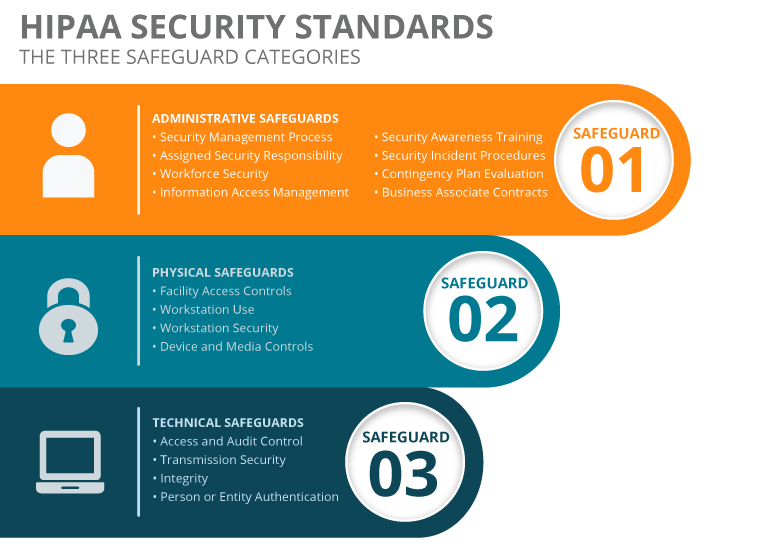
Spanning from employee training to encryption, these standards attempt to protect patient information from different threats. Some standards are required, while others are just recommended.
If you are qualified as a “covered entity,” required standards must be implemented, or else your business may be liable and investigated for breaching regulations. What are the consequences of not maintaining HIPAA compliance?
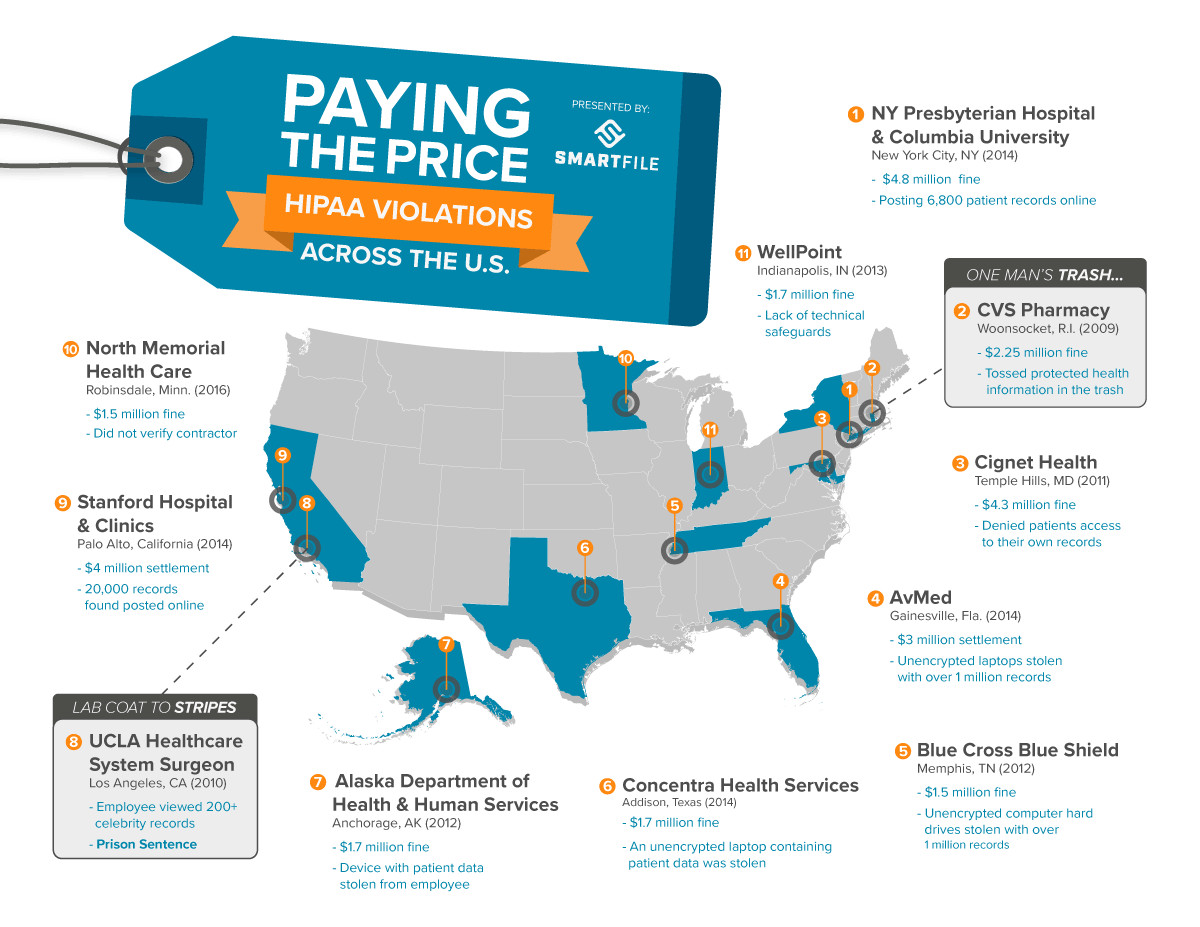
The Department of Health & Human Services isn’t messing around. While these are just the most infamous examples of HIPAA violations, there are hundreds of violation investigations and reports annually. So, what steps can your IT department take to become HIPAA compliant?
HIPAA 101: Breaking Down HIPAA Compliant File Sharing
Within the three safeguard categories (administrative, physical and technical) lie a myriad of IT-related regulations and concerns. For the purpose of this article, we will focus primarily on the technical safeguards, which largely affect file sharing.
The Security Rule defines technical safeguards as “The technology and the policy and procedures for its use that protect electronic protected health information and control access to it.” Within the technical safeguards, there are four criteria:
- Access and Audit Control
- Transmission Security
- Integrity
- Person or Entity Authentication
The Security Rule was intended to be “technology neutral” as to not endorse any one product or methodology. Thus, how organizations specifically implement HIPAA compliance is up to them. However, covered entities must use their utmost discretion in choosing products that uphold HIPAA compliant file sharing standards.
1. Access and Audit Control
Access controls offer three actionable items: unique user identification, emergency access procedure, automatic logoff and encryption/decryption.
REQUIRED: First, unique user identification is a required protocol. Each employee or user must have an assigned unique name or number for identifying and tracking any actions associated with their role.
Furthermore, finding a platform with granular permissions allows IT to manage who has access to different directories. In file sharing, granular permissions dictate who can share or manage any given file or folder.
Second, an emergency access procedure is required. In the case of an emergency, an established plan is necessary to access electronic Personal Health Information (ePHI). While this does not necessarily affect business associates, covered entities must consider a backup or emergency failover solution for ePHI.
Third, audit controls are required. Audit controls may be in the form of hardware, software and/or procedural methods. These controls must monitor any activity in devices or networks that contain or use ePHI. In file sharing, this most often takes the form of user analytics.
RECOMMENDED: Some protocols are not required, but rather a preventative measure to ensure the safety of the covered entities’ networks and clients’ PHI.
Automatic logoff comes highly recommended. Automatic logoff is defined as terminating a session after a predetermined period of time has elapsed. This safety feature makes it more difficult for unauthorized employees to access data. Furthermore, this feature is automatically built into most software, making it easy to implement.
Encryption and decryption implementation can also further protect ePHI from data breaches or hackers. While not required, this actionable item comes highly recommended, and may save covered entities from further problems down the road.
2. Transmission Security
Transmission security aims to protect all data during the course of transmission on a network. Information that is cloned, altered or deleted can result in non-cohesive data or worse, endangering patients.
RECOMMENDED: In the Security Rule, HHS recommends reviewing internal procedures and searching for flaws. Then, implement a transmission security plan that best suits your organization.
The best way to do this is by approaching the existing methodology used for transmitting patient information: email, the Internet and in-person and assessing the existing flaws.
Integrity Controls implement security measures that protect data sent electronically. These controls ensure that the original data cannot be modified (especially improperly) without detection or alerting the data owner. Integrity controls can take multiple forms, including granular permissions that prevent outsiders from viewing the information.
Encryption once again makes the list of recommended protocols. Encrypting data during transmission is generally a sound security practice.
3. Integrity
Integrity is the protection of data so it cannot be trashed or edited without proper authorization. Integrity calls for transmission security. Yet, when transmission security fails, there must be a second protocol to assess if the information is still accurate.
RECOMMENDED:
A Mechanism to Authenticate Electronic Protected Health Information can include digital signatures or checksum verification. When transmission fails, the HHS recommends a secondary authentication procedure.
4. Person or Entity Authentication
REQUIRED:
Authentication is required to verify that entities or persons accessing ePHI are who they claim to be. An everyday example of authentication is having employees use their social security number, employee ID, or thumbprint to clock in and out of work.
Choosing a HIPAA Compliant File Sharing Solution
When searching for a HIPAA compliant file sharing solution, be on the lookout for:
- Encryption and Decryption
- User Auditing
- Granular Permissions
- Password Protected Sharing
- User and Password Management Tools
- Firewalls or Backup
HIPAA regulations can be very subjective in the actual implementation of technology. Therefore, the term HIPAA compliance can mean different benchmarks for each organization that must comply with them.
Some covered entities require that file sharing or cloud platforms sign a Business Associate Agreement (BAA). There is no template for this agreement, but rather, the covered entity outlines the specific requirements a file service must meet.
However, in the cases where a BAA is not required by the covered entity, a HIPAA compliance statement may be due. This statement can simply be a checklist of the features or actions a business associate is expected to maintain during their work together.
SmartFile offers a signed HIPAA compliance statement available upon request and can also sign a BAA agreement (included for free in the subscription for select plans only). Our platform combines the HIPAA compliant technical safeguards into a brandable, web interface solution accessible from any portable device.
For covered entities or business associates HIPAA compliant file sharing can seem neverending. However, with the right policies and technology, your firm can dodge the perilous flying monkeys and complete your journey on the Yellow Brick Road of compliance.
Looking for a HIPAA Compliant File Sharing Service?
Need Enhanced Security?

Want to Control Costs?

