- Introduction
- What is IP?
- Identifying Your IP
- What is IP Theft?
- How to Protect Your IP
- Solutions
- Infographic
There are 318.9 million people in the United States and their collective creativity is one of the most economically beneficial assets in the country.
That collective creativity, when funneled into a commercial purpose is called intellectual property (IP). Just as valuable as physical property, the protections of IP, called intellectual property law, help to fuel innovations in the United States. With these protections, inventors and creators feel safe to manufacture and share their ideas with the world.
While this system has worked reasonably well for the last 200 years, the rapid pace of technology and those who exploit its weaknesses has made intellectual property more vulnerable than ever.
There currently exists a contract between the U.S. and Chinese governments (the latter an ever-present threat to U.S. IP). Ideally, this contract is supposed to stanch the unauthorized and illegal flood of IP to China and minimize the billions of dollars lost to these sanctioned cyber security attacks.
However, since the 2015 agreement, not much has changed. Chinese hackers continue to target corporate IP, stealing secrets and pricing data from the United States Steel Corp and wriggling their way into remotely controlling a Tesla Model S. It appears that the problem with China is not going away.
This article is not intended to get into U.S.-China cybersecurity relations, but to make business owners and corporate leadership aware of just how much of a problem IP theft in the digital age has become.
Keep reading and you’ll learn the basics of intellectual property as well as the law that protects it and what companies can do to fight back against those who seek to harm.

What is Intellectual Property?
“Intellectual property, very broadly, means the legal rights which result from intellectual activity in the industrial, scientific, literary and artistic fields.”
First, let’s explain what intellectual property is. Intellectual property has been described as “creativity of the mind” which, in layman’s terms, means ideas, inventions, formulas, methods, manufacturing procedures and any other idea specific to a creator or company that is used for commercial purposes.
In order to protect these items, we have intellectual property law. The four main branches of intellectual property law are trade secrets, copyrights, patents and trademarks. Let’s break each of these down into their descriptions, what they cover and what legal intellectual property protection avenues exist.

Trade Secrets
You may be drinking one of the most famous trade secrets right now — a Coke. The formula for Coca-Cola is heavily guarded; legend says only 3-4 executives know it at a time and they all fly separately. In reality, it’s more likely several key people know the recipe or we wouldn’t all be able to drink a Coke whenever we wanted.
The official definition of a trade secret, separated into its two essential parts:1. information, including a formula, pattern, compilation, program, device, method, technique, or process, that derives independent economic value, actual or potential, from not being generally known to or readily ascertainable through appropriate means by other persons who might obtain economic value from its disclosure or use;2. and is the subject of efforts that are reasonable under the circumstances to maintain its secrecy.
It’s important to understand these two distinctions, and the second is vital for nearly all intellectual property:1. a trade secret must be unique and proprietary and give one company an edge over another company’s product or process and be, of course, a secret;2. a company must do its best to protect the trade secret. Trade secrets (and all IP) must be protected to the best ability of the company or individual and when threatened, must be defended or it will be lost.
In addition to recipes, trade secrets can also be drug formulas, manufacturing methods or even an algorithm. The process that goes into creating The New York Times Bestseller List is even a trade secret.
Trade secrets are very valuable to companies, not just for the trade secret itself, but for everything that accompanies it, which we will get into later. Trade secrets were not covered by federal law until recently, but have historically been overseen by state legislation and are protected upon registration.

Copyrights
A copyright is the one legal protection that is immediately bestowed upon the creator once their work is in a tangible form. An artist’s canvas, a writer’s novel, a videographer’s film, even derivative works — these are all protected by copyright law.
While a copyright is automatically granted to these works, it is up to the creator to defend that work and the first step will be registering their copyright with the U.S. Copyright Office. If not registered, there is little-to-no legal recourse a creator can take to defend their work.

Patents

The first patent ever was filed in 1790 by a man named Samuel Hopkins. He was seeking patent protection for a process that he invented to make a fertilizer ingredient called potash. Since then, patents have been filed for everything you can think of, ear protectors that keep long-eared animals’ ears out of the way during mealtimes to a high-five machine.
While they sound similar, patents are far different from trade secrets. First, a patent gives the right for the patent holder, and only the patent holder, to manufacture their product for a period of 20 years; after that, anyone can use the plans to create the product.
Second, when patents are filed, they must include the inventor’s detailed plans and be made publicly accessible. This means other inventors can access the patent at any time, make improvements to it and release their own product. However, the process for filing a patent can be long, complicated and often require the help of a patent attorney.
Patents are also very valuable. When Yahoo put up 3,000 patents for bid in the summer of 2016, they expected to net somewhere around billion, with outside estimates expecting anywhere from billion to billion.

Trademarks
You see trademarks every day, from the Nike Swoosh on your shoes or clothing to the colors of a college or professional football team’s uniform (See: Texas University, Pantone color #159). For something to become a trademark, it must be both used in commerce and it also must be distinctive. Once it’s accepted as a trademark, the owner has exclusive rights to it.
A trademark protects more than just the symbol or image it’s made of. It protects the brand and the reputation of the owner or business, as well as the customers who trust the brand.
LaCoste, a brand that’s been around for several decades, has had its share of branding troubles. In the 1980s, it was overshadowed by the Izod brand and took nearly a decade to recover before rising back in popularity to the high-end brand it is today. As well, it’s a brand that is forever being bombarded with copycat and lookalike brands trying to take a slice of its market. Lacoste does this because if they don’t defend their trademark, they can lose it.
Wait, What Does Your Intellectual Property Look Like?
You just got through a brief overview of intellectual property and while you may be familiar with these terms, you may not be as familiar with your own IP. How do you identify IP when it’s not so easy to spot as a recipe, logo or book?
Let’s revisit Coca-Cola’s trade secret. The “medicinal” recipe (and possibly the 9 milligrams of cocaine in each glass) was what first attracted consumers to it.
In the century since, the alleged recipe has been revealed several times (at least once in a 2011 episode of This American Life) and yet the majority of people aren’t running bathtub Coca-Cola-making operations in their homes. This is because, through branding and marketing efforts, Coke has built an incredibly brand-loyal customer base who are so attached to Coke won’t drink anything else, even when it’s purportedly better than Coke.
These branding and marketing efforts are part of Coca-Cola’s protected intellectual property, even though they aren’t nearly as famous or legendary as the origin story of its eponymous soda.
It’s that IP, constantly collected and reworked to build brand loyalty, that makes Coca-Cola so successful and profitable. If another company were to have that data on how to target Coca-Cola’s customer base, then they might be able to start chipping away at Coke’s market share.
Identifying Your Intellectual Property
Your business may be more of a small-batch soda producer than a Coca-Cola, but it’s still important to identify the underlying IP of your product or methods.
According to Vikas Bhatia, the founder and CEO of cybersecurity firm Kalki Consulting, many businesses are overlooking some of their most important data.
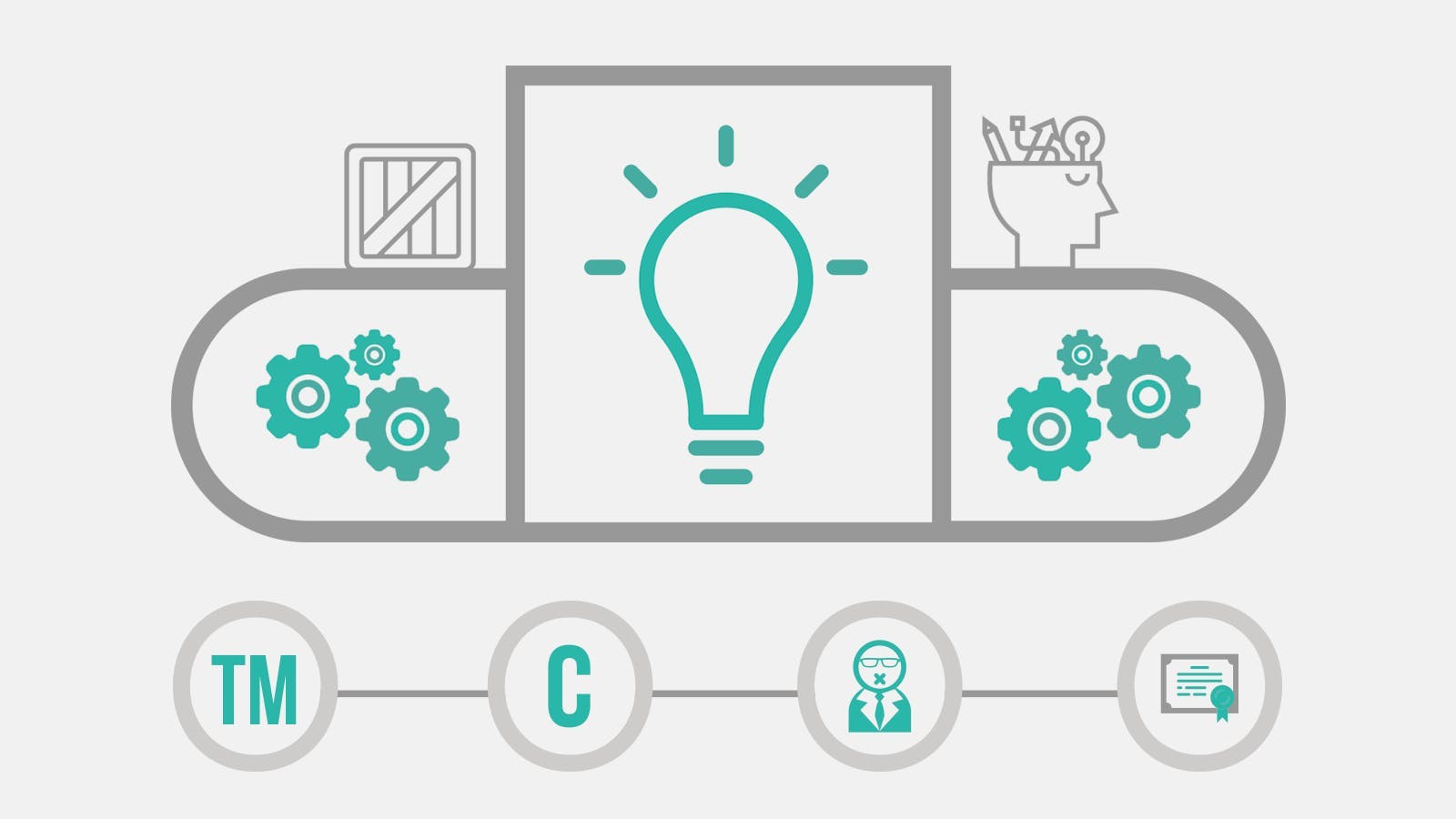
“What’s more important, Google’s search code or Google’s search data?” says Bhatia. While many may think that Google’s trade secret, their algorithm, is the key to their success, it’s only a part of it. The algorithm itself is pretty well-known, but the user data and keyword-based advertising they sell alongside their search results is what made them 7.39 billion in 2015.
He goes on to say that businesses need to think more critically about the information that drives their specific business and how to protect it. For instance, he says companies will protect their credit card data but they will be remiss in monitoring how a third-party vendor connects into their network.
This is exactly what happened to Target, who suffered a major breach in 2013 because a small Pennsylvania-based heating and air conditioning firm they worked with had been infected with malware. Using credentials snagged in that breach, the hackers were able to access Target’s network.
“The first thing to do is have someone take a look at your organization and work out what is the data that drives the organization.” says Bhatia. “Where is that data coming from? What you do you once you have it? Where does it go? Are you giving it to certain parties? Many parties now have an offshore team, many organizations have a vendor with offshore teams, so is your proprietary data going overseas?”
This is just a start to identifying your intellectual property. Since many hacks are opportunistic, it’s vital to identify all of your essential and important data before a breach happens, whether it’s in-house or with a cyber security consultant. A proactive approach to intellectual property protection now will very possibly keep your business from losing everything.

The Value of IP
Most successful companies understand the inherent and actual value of the IP they’ve identified. But there is another entity who values that IP for different reasons. Countries like the U.S. don’t just have IP laws to protect creators, but to protect that creativity and its market benefits.
The theory goes that if the government stands behind these creators and their work, it will “encourage fair trading which would contribute to economic and social development,” says the World Intellectual Property Organization.
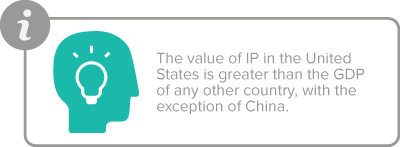
According to a recent article in Forbes, the value of the IP in the United States is greater than the GDP of any other country, with the exception of China. Looking to the Intellectual Property Protection and the U.S. Economy: 2016 Update, there are 81 industries that are “IP-intensive” and these industries alone accounted for 9.7 million jobs in 2014, as well as .6 trillion in added value. Not to mention the 15.2 billion brought in from licensing alone.
Countries have laws for intellectual property protection for two main reasons:One is to give statutory expression to the moral and economic rights of creators in their creations and the rights of the public in access to those creations.The second is to promote, as a deliberate act of Government policy, creativity and the dissemination and application of its results and to encourage fair trading which would contribute to economic and social development. — WIPO
What are these IP-intensive industries? They are industries that have a large amount of business or employment related to either patents, trademarks or copyrights. Trademark-intensive in are the largest under the IP umbrella and provide 23.7 million jobs. These industries add to the GDP of the U.S. by providing a large portion of the total imports and exports of the U.S. Pharmaceuticals and medicines export 4.5 billion in merchandise, while software publishers are the highest of the service-providing industries with 2.7 billion in exports.
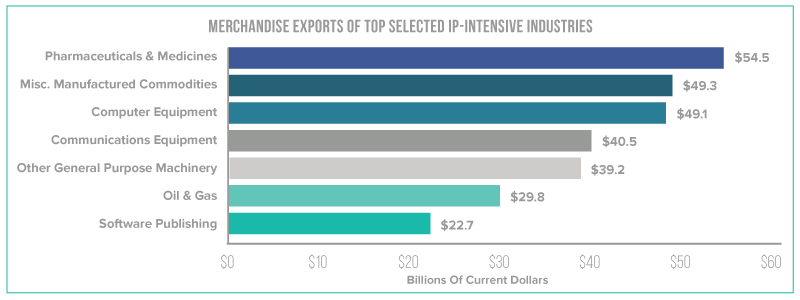
So, you get it — IP is valuable to more than just your company. And that’s what makes it even worse when it’s stolen. Whether Chinese hackers or negligent employees, read on to see how both are part of the IP theft problem.
What is Intellectual Property Theft?
Spoiler alert: once your IP is stolen, it’s gone.
This affects every business, but for those small-to-medium businesses that specialize in one product or area, IP theft can be devastating. What are the most common methods of IP theft?

Negligence and Ego as Contributors to Intellectual Property Theft
It’s likely impossible to count every instance of employee negligence contributing to data leaks and breaches, but it happens all of the time.
As Bhatia sees it, there are two different types of internal threats. The first is unintentionally malicious, where employees are negligent. For instance, not thinking when clicking on links in emails that contain phishing attacks or sending spreadsheets containing sensitive financial data to their personal computer to do some work at home.
“What that means is, I could be lazy. I don’t have the intent to bring harm to the organization, but the end result is malicious activity,” says Bhatia.Without proper training, employees may not even be aware they are engaging in Shadow IT or social engineering scams and putting the company at risk.
The second threat can be malicious with intent. This can encompass employees downloading proprietary data to intentionally transfer it to a competitor, or business partners turning on each other by taking their IP and starting a new venture with it, cutting out the other partner. According to Bhatia, this happens, but less than unintentional malicious events occur.
Another part of unintentionally malicious can be boiled down to ego. When Bhatia serves as a cybersecurity consultant for clients, his suggestions are often met with resistance. “There’s a certain defensiveness. No one knows their business like them, so, who [am I] to come in and tell [the company] about it?” He goes on to say that if certain teams are in charge of systems and data, they may be reluctant to admit they haven’t been doing everything they can to protect data.
Lastly, we can all fall victim to Ostrich Syndrome. We can be so deeply under the spell of wishful thinking that we think data breaches and hacks will never happen to us, even though nothing has been done to prevent them. This is a major problem if you’re aiming for air tight intellectual property protection.
Your IP as the Intentional Target of Hackers
International hacks are the hacks we often hear about in the news. They involve the hackers that are intentionally — whether government-ordained, criminal or just a handful individuals with a purpose — targeting the IP of corporations and businesses.
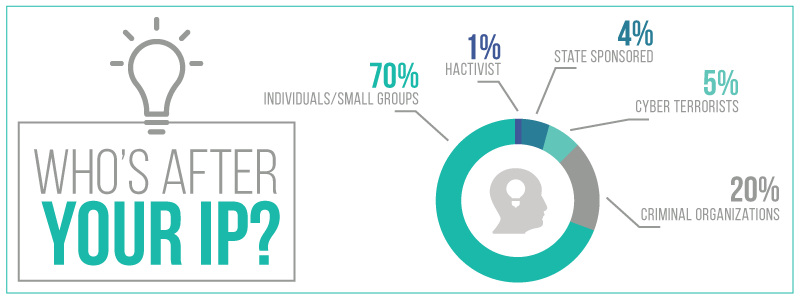
Source: Easy Prey
By trying to understand why a hacker would target your IP, it may help you identify your intellectual property and its vulnerabilities. What is their motivation? What’s their endgame? Let’s break down some types of hackers and their motivations.
We’ve discussed the hacker mentality in a previous blog post by Nick Espinosa. You can read the whole thing here, but below is a high-level version of why hackers do what they do.
The Hacktivist
As the name suggests, these are “hacker activists.” They believe in social justice causes and they are able to pool together a large amount of individuals with shared beliefs to attack targets.
The “Mount Everest” Hacker
These people are climbing the mountain because it’s there. While their intentions aren’t often malicious, they hack systems and networks simply to see if they can do it.
The Hired Gun
This is a mercenary, typically found on the dark web. If you need someone with a particular set of skills, this is a place where you can find someone to execute your task for a price. They are motivated by money, with a lack of ethics that make them particularly dangerous.
The Wronged
This type of hacker can be devastating to intellectual property, typically because they feel their employer (you) has wronged them in some real or imagined way. Because they know your policies and systems, they have a head start and a big chip on their shoulder.
The Government Employee
These groups execute hacks on behalf of a government entity for an array of reasons. This type of hacker can be especially dangerous from an intellectual property perspective, because they may be encouraged to access the IP of businesses in other countries.
These are only a handful of the categories of hackers, but knowing their motivations can get you a step ahead in protecting your IP. Now that we’ve covered some types of hackers, let’s talk about what can be done once your intellectual property has been exposed to an outside party.

Oh, the Humanity: What Can be Done When Your IP is Gone
In short, not much.
If you have taken steps to enhance intellectual property protection, like registering copyrights, creating confidentiality documents and policies around trade secrets and securing your IP to the best of your ability, you have a better chance at lessening a data breach or theft and the damages that could follow.
“My recommendation to businesses is really two-fold. One, what are your legal protections, and two, what are your technological protections?” says Anthony M. Verna III, attorney-at-law and managing partner at Verna Law, P.C. “Make sure you work with not just the law firm but with an IT company.”
Verna adds that businesses should be sure to make a trade secret agreement with employees, “If what’s important to the business is a trade secret, it has to be stated that it’s a secret. If there is some sort of internal company way of marking something as a trade secret or confidential, it needs to be done.”
For those who discover that their IP has been breached and stolen, there’s not much that can be done, says Verna, “The problem is that once it’s out of the bag, it’s out of the bag, even from a legal standpoint.”
What can be done, Verna advises, is to seek punishment internally in the form of monetary damages for those who have intentionally or unintentionally let business secrets out.
Fortunately or unfortunately, investors can also sue — if a business doesn’t do everything they can to fortify intellectual property protections, they are not operating in the best interest of the business and the investor can sue to get their investment back, plus damages.

These types of punishment will be civil, not criminal, meaning you can’t exactly send the former or current employee to prison for their wrongdoing. “Whether somebody hacks your network and steals your trade secrets or is an employee who steals trade secrets, there’s not much of a civil difference there,” says Verna.
If you need to prosecute a trade secret theft from a criminal standpoint, a business will need to consult with the FBI. At that point, you’ll file a report with them and they will run with the case. However, that doesn’t guarantee justice.

An Ounce of IP Theft Prevention…
The best defense is a good offense, as the saying goes.
A company who has been breached needs to have evidence of the breach. Many small businesses, says Verna, don’t hire IT vendors or have the capability or capacity to track the activity or access of their data.
“Having professional [IT] backing is important because then you have a business that stores data all the time, that tracks logins all the time and tracks the data all the time,” says Verna, “Then you actually have evidence. If you can get an IP address, you’ll be golden.”
This is where built-in analytics tools that monitor files are helpful, because they provide auditing and activity reporting to help identify what happened. These tools can go beyond the username to the IP address, date, time and access location.
To avoid being sued by investors or others, a business should try to do everything it can to fortify intellectual property says Verna. This includes safeguarding data and trade secrets with passwords, encryption and employee contracts.
Additionally, if you do business across international borders, make sure your IP is registered within that country, which will make it easier to file a suit in that country.
Now that we’ve briefly covered legal aspects of IP theft, let’s learn how to safeguard and build intellectual property protections from a technical perspective by keeping hackers out in the first place.
Creating Robust Intellectual Property Protections
Let the Right One In: Protect the Perimeter to Safeguard Your IP
More Strategies to Protect Your Intellectual Property
Using a brand new type of firewall or changing the way your network is set up is important and will take some time to implement. If you are looking for a few things you can do immediately to combat intellectual property theft, check out the steps below, especially if you’re an SMB who can’t exactly afford to break the bank on security.
Here are some ways you can decrease the risks of intellectual property theft without adding many new tools or procedures.
1. Establish Baseline Metrics
Use analytics tools to understand what typical usage looks like on your network so you can identify outlying behaviors and create alerts around this activity.
2. Set Up an IT Employee Exit Checklist
When employees leave, make sure logins and access to all programs are removed. This can seem daunting to do every time someone leaves, but it’s important in preventing unwanted access. Don’t be afraid to consult an employee exit checklist to help you remember.
3. Educate Employees About Internet Risks
According to cybersecurity book Easy Prey, 45% of employers don’t provide Internet safety training to their employees. Check out resources on common cybersecurity issues like social engineering attacks and ransomware to educate employees.
4. Create Usage and Internet Policies
Each department should not have a different security policy. Assign one person to oversee security policies and contracts. It could be HR, a CSO or CIO, as long as employees know where to turn for security policies and issues.
5. Setup Remote Access Policies and Education
When working from home, employees can get a little lax on security. Educate remote employees about what they can and cannot do from their home or makeshift on-the-road offices.
6. Device Upload and Download Procedures
Malware that can capture credentials or share intellectual property is easily downloaded. Create procedures to ensure that devices connected to the network are required to get explicit permission from the user or administrator to download or install.
7. Backup Anything Important
Whether it’s a company blog or a tiny dataset, if it has any value to your organization, it’s worth backing up and ensuring those backups work.
8. Double Check Access Permissions
In larger networks, it’s easy for users to slip through the cracks and have access to areas they shouldn’t. Granular and regularly updated user permissions go a long way in protecting data.
Not all of these suggestions are technical, so they may be easier to implement by non-tech staff. If you are concerned about the cost of the technical suggestions, don’t buy what you don’t need, but do make sure you choose tools that employees will use (i.e., something as close to their typical work routine as possible), but also ones that provide oversight of activity for IT.

Why Usability is Crucial for Intellectual Property Protection
When you’re solely focused on technical, it may be easy to lose sight of how the users work with the product, a.k.a usability. A product that works on the technical side may seem perfect and secure from an IT perspective, but if employees find it slows down their work or is difficult to use, they’ll abandon it.
In fact, a major cause of internal data leakage is simply an employee using a consumer-grade tool to get their job done more efficiently. This tool could be a Dropbox account or unencrypted email, neither of which have enterprise-level protections. Chances are, IT doesn’t know the technology is being used, so they can’t secure it against threats.
The tools your business uses to manage intellectual property need to be simple and fully functional from the employee perspective, as well as IT’s. These tools include everything from VPN access to simple file sharing methods.

Smarter Intellectual Property Protection
After securing your perimeter and integrating as many protections as you can for your intellectual property, try closing the internal leaks as well. One of the best ways to do this is to replace the tools employees use that allow for the most vulnerability — the methods of sharing files that contain IP and the storage that holds these files.
Ideally, you’ll want to choose a tool that combines file sharing, storage and central tracking and analytics for the movement and activity of those files that contain information that has to do with trade secrets, research data or anything sensitive that’s also essential to a company’s success and profitability.
There are tools out there that offer the all-in-one offerings of file sharing, storage and analytics, but when managing IP sharing and storage day-to-day, few of these tools will actually serve both IT control and visibility as well as employee usability.
In an ironic twist, SmartFile was originally considered a Shadow IT tools. Not the tool that combats Shadow IT, but the unapproved tool that employees used to speed up their work and increase their productivity.
After entire departments started using it and IT got wind of it, SmartFile went full circle and was adopted as both a productivity tool and a tool to combat Shadow IT. Eventually, SmartFile evolved into the complete file management tool entire organizations use today.
Usability is bettered by the variety of access methods, allowing employees to connect and share however they want, whether it’s from the branded and responsive online portal, an FTP client, their native file explorer or custom-created API connections.
Governance is bettered with administrative tools that monitor the flow of intellectual property between parties and allow for better permissions and access rules. The analytics tools include audit log information, activity tracking and user tracking. Have another tool for reporting? SmartFile offers syslog export, too.
If IT prefers a more visual approach to dissecting data, the SmartStats interactive visual dashboard will help them better grasp outlying behavior and activity from users and files.
Multiple layers of firewall technologies within the device itself protect the data inside. With on-prems, companies get complete control of the encryption keys. This ensures that only the people who have access can decrypt the code, helping to ensure intellectual property protection.
Need even more options? SmartFile can act as an enhanced cloud-enabled file server that sits behind your firewall or it can be a simple file hosting and sharing provider. How your business deploys it and uses it is up to you.
Because SmartFile can work as an all-in-one, it delivers a great solution for organizations looking for the auditing, protection and day-to-day management of IP.
Nervous? Start Now to Protect Your Business IP
Hackers will keep taking advantage of the intellectual property of U.S. businesses as long as we continue to allow them to exploit the vulnerabilities of our networks and systems. Businesses must do everything in their power to enhance intellectual property protection, especially from attacks that can weaken and diminish the creative contributions of the nation’s population.
This includes securing the perimeter of your network and systems with modern firewalls that follow the Zero Trust Model; implementing security policies and confidentiality contracts with employees and making sure they understand the consequences of intentional or unintentional data breaches; and installing monitoring and tracking tools for your IP.
It’s unlikely that data breaches and IP theft will ever be eradicated, or that even the most stringent intellectual property protections will eliminate all threats. Human nature will always be a vulnerability and hackers will always find a new way in. But the more we can do to secure our IP now, the more we can minimize these attacks recurring. If you’re even a little bit worried about your IP, now is the time to take action, whether it’s consulting with SmartFile about our on-prem file management and analytics platform or drafting security policies for your employees —
start right now.


Intellectual Property Protection & Insight Infographic